Kali Linux - NetAttack2
click here to get free money
NETATTACK2
NETATTACK2 is a script written in python that can scan and attack networks. It is GUI-based which makes it easy to understand.
What can I do with it?
SCANNING
- Scan your network for active hosts, their operating system, open ports and way more.
- Scan for Access-Points and figure out encryption type, WPS and other useful data.
SPOOFING/SNIFFING
- Simple ARP Spoofing
- DNS Sniffing by ARP Spoofing the target and listening to DNS-Queries
KICKING
- Kicking hosts off your internet using ARP-Spoof attack
DEAUTHING
- Send deauthentication packets to Access Points in your area (DoS)
- Deauth-All, basically does the same but it scans for networks and attacks them periodically.
What do I need? (Requirements)
- Python
- Linux (Kali Linux prefered)
- Required modules can be installed at runtime
TorGhost | Surf Anonymously - Tor Anonimizer
click here to get free money
-----------------INSTALL ---------------------------------------------------------------- clone to the repo or download the files, open the directory and follow the commands
# chmod +x install.sh
# ./install.sh
_____ ____ _ _
|_ _|__ _ __ / ___| |__ ___ ___| |_
| |/ _ \| '__| | _| '_ \ / _ \/ __| __|
| | (_) | | | |_| | | | | (_) \__ \ |_
|_|\___/|_| \____|_| |_|\___/|___/\__|
v2.0 - SusmithHCK | www.khromozome.com
USAGE:
torghost start -----(start torghost)
torghost stop -----(stop torghost)
torghost switch ----(switch IP)
click here to get free money
☠ ★ Devploit . version 1.1 ☠
Author: Joker-Security [ dev-labs ]
★ Description:
Devploit is a simple python script to Information Gathering
★ Download:
● git clone https://github.com/joker25000/Devploit
★ How to use:
cd Devploit
chmod +x install
./install
Run in Terminal
Devploit
★ Properties :
● DNS Lookup ● Whois Lookup ● Revrse IP Lookup ● GeoIP Lookup ● subnet Lookup ● Port Scanner ● Extract Links ● Zone Transfer ● HTTP Header ● Host Finder ● IP-Locator ● Update tool ● About !!! ● Exit
★ Screenshot:
★ video tutorial:
4nonimizer | Surf Anonymously
click here to get free money

What is 4nonimizer?
It is a bash script for anonymizing the public IP used to browsing Internet, managing the connection to TOR network and to different VPNs providers (OpenVPN), whether free or paid. By default, it includes several pre-configured VPN connections to different peers (.ovpn files) and download the credentials (if the corresponding provider support it). Also, it records each used IP that we use every 300 seconds in log files.
This script is enabled as a service in systemd systems and uses a default vpn (VPNBook) at system startup.
Since version 1.06 the dns resolution requests are done throught DnsCrypt (enable and disable with option enable_dns or disable_dns)

Attention VPN Providers!
If you are a provider, you support OpenVPN and want your VPN to be integrated into 4nonimizer contact the developers at hackplayers @ ymail.com.
Installation
Download the repo using git, execute the command ./4nonimizer install in the directory, and follow the screen instructions, 4nonimizer will move to the directory /opt/ and installed as a service.This script has full compatibility with Kali Linux, although it has been properly tested and should also work on other distributions like Debian, Ubuntu and Arch (Manjaro). However there could be some bugs, or unexpected performances (please comments if you find any!).
Options
Once installed 4nonymizer, enter the command 4nonimizer help to get the help, which shows all the available parameters: ___ _ _
/ | (_) (_)
/ /| |_ __ ___ _ __ _ _ __ ___ _ _______ _ __
/ /_| | '_ \ / _ \| '_ \| | '_ ` _ | |_ / _ \ '__|
\___ | | | | (_) | | | | | | | | | | |/ / __/ |
|_/_| |_|\___/|_| |_|_|_| |_| |_|_/___\___|_|
By Carlos Antonini & Vicente Motos
Version: 1.06-beta
Usage: 4nonymizer <parameter>
install: Install the script in run services
uninstall: Disable run service and remove app directory
change_provider: Change VPN Provider
change_ip: Change IP from VPN current
vpn_status: Check IP and provider VPN running
update_vpns: Update all ovpn of VPNs
start: Init the 4nonimizer service
stop: Stop the 4nonimizer service
stop_nonet: Stop the 4nonimizer service and shutdown network interfaces
restart: Restart the 4nonimizer service
update_app: Update this program via git
privoxy: Install and configure privoxy with port 8118 (BETA)
proxychains4: Install and configure proxychains4 for default in the system
browser: Fire up a firefox browser with profile privoxy -> tor
test_availability: Check peers availability and delete ovpn file if the IP/service is unreachable
location: Now you can select a specific country or continent of the vpn peer
enableboot: You can enable service in boot
disableboot: You can disable service in boot
enable_dnscrypt: Enable dnscrypt service
disable_dnscrypt: Disable dnscrypt service help: Help (this screen)
___ _ _
/ | (_) (_)
/ /| |_ __ ___ _ __ _ _ __ ___ _ _______ _ __
/ /_| | '_ \ / _ \| '_ \| | '_ ` _ | |_ / _ \ '__|
\___ | | | | (_) | | | | | | | | | | |/ / __/ |
|_/_| |_|\___/|_| |_|_|_| |_| |_|_/___\___|_|
By Carlos Antonini & Vicente Motos
Version: 1.06-beta
install: Install the script in run services
uninstall: Disable run service and remove app directory
change_provider: Change VPN Provider
change_ip: Change IP from VPN current
vpn_status: Check IP and provider VPN running
update_vpns: Update all ovpn of VPNs
start: Init the 4nonimizer service
stop: Stop the 4nonimizer service
stop_nonet: Stop the 4nonimizer service and shutdown network interfaces
restart: Restart the 4nonimizer service
update_app: Update this program via git
privoxy: Install and configure privoxy with port 8118 (BETA)
proxychains4: Install and configure proxychains4 for default in the system
browser: Fire up a firefox browser with profile privoxy -> tor
test_availability: Check peers availability and delete ovpn file if the IP/service is unreachable
location: Now you can select a specific country or continent of the vpn peer
enableboot: You can enable service in boot
disableboot: You can disable service in boot
enable_dnscrypt: Enable dnscrypt service
disable_dnscrypt: Disable dnscrypt service
Available VPNs
Currently it supports the following VPN providers:- HideMyAss https://www.hidemyass.com/- TorGuard https://torguard.net/- VPNBook (by default) http://www.vpnbook.com/- VPNGate http://www.vpngate.net/en/- VPNMe https://www.vpnme.me/- VPNKeys https://www.vpnkeys.com/- FreeVPN https://freevpn.me/- TunnelBear https://www.tunnelbear.com/- Cryptostrom https://cryptostorm.is/- SlickVPN https://www.slickvpn.com- 7Proxies https://www.7proxies.com/- StrongVPN https://strongvpn.com/- NordVPN https://nordvpn.com- Vyprvpn https://www.goldenfrog.com/es/vyprvpn- ExpressVPN https://www.expressvpn.com
Install a new VPN
To install an additional vpn we have to use the following structure in order to the 4nonimizer be able to integrate and perform operations with it.First, we have to create the following dir structure /vpn/ within 4nonimizer path:In our example we create the folder /vpntest/ and within it placed all .ovpn files we have. If the files ovpn not have the certificate within each of them we put in the same folder as shown in the example certificate.crt.In addition, we must place a file named pass.txt containing 2 lines: the first one with the username and the second one with the password, as shown below:If we have correctly performed all steps when we execute the command 4nonimizer change_provider the menu will show our vpn:As you can see in the picture, option [7] it is the vpn we've created.
Getting credencials and ovpn files automatically
If the VPN provider allows automation of credential and/or .ovpn files getting, 4nonimizer has standardized the following scripts names and locations:- /opt/4nonimizer/vpn/provider/vpn-get-pass.sh- /opt/4nonimizer/vpn/provider/vpn-get-ovpn.sh4nonimizer automatically detect the presence of both scripts and indicate (Auto-pass Login) or (Auto-get OVPN) if it finds in the first line of each file the expression '#4uto' or '#m4nual' depending on the performed actions.
Extras
- Execute 'source 4nonimizer' to activate autocompletation of parameters.
- Copy .conkyrc in your home directory to load a 4nonimizer template and execute conky.
- Copy .conkyrc in your home directory to load a 4nonimizer template and execute conky.
References
- http://www.hackplayers.com/2016/08/tuto-enmascarar-ip-linux-vpn-tor.html
- http://www.hackplayers.com/2016/10/4nonimizer-un-script-para-anonimizar-ip.html
- http://www.redeszone.net//2016/10/07/4nonimizer-te-permitira-automatizar-la-conexion-diferentes-vpn-anonimizar-ip/
- http://www.kitploit.com/2016/10/4nonimizer-bash-script-for-anonymizing_10.html
- https://www.digitalmunition.me/2016/10/4nonimizer-bash-script-anonymizing-public-ip-managing-connection-tor-different-vpns-providers/
- http://www.hackplayers.com/2016/10/4nonimizer-un-script-para-anonimizar-ip.html
- http://www.redeszone.net//2016/10/07/4nonimizer-te-permitira-automatizar-la-conexion-diferentes-vpn-anonimizar-ip/
- http://www.kitploit.com/2016/10/4nonimizer-bash-script-for-anonymizing_10.html
- https://www.digitalmunition.me/2016/10/4nonimizer-bash-script-anonymizing-public-ip-managing-connection-tor-different-vpns-providers/
Videos
- Instalar 4nonimizer Kali Linux https://www.youtube.com/watch?v=FQRuRmMkcDg
- 4nonimizer Navegando de manera segura VPN (Kali Linux 2016.2) https://www.youtube.com/watch?v=6GApaN7fSn8
- devenir anonyme sur kali linux (4nonimizer) https://www.youtube.com/watch?v=Y3puD1Bw3xA
- Anonymizer - How To Hide Your IP address on Kali Linux 2016.2 (Change IP) https://www.youtube.com/watch?v=MNdQD0DCG0A
- Become Anonymous on kali linux 2016.2 https://www.youtube.com/watch?v=IFnhm-rrnEg
- 4nonimizer Navegando de manera segura VPN (Kali Linux 2016.2) https://www.youtube.com/watch?v=6GApaN7fSn8
- devenir anonyme sur kali linux (4nonimizer) https://www.youtube.com/watch?v=Y3puD1Bw3xA
- Anonymizer - How To Hide Your IP address on Kali Linux 2016.2 (Change IP) https://www.youtube.com/watch?v=MNdQD0DCG0A
- Become Anonymous on kali linux 2016.2 https://www.youtube.com/watch?v=IFnhm-rrnEg
Versions
| Number | codename | date |
|---|---|---|
| 1.00-beta | .bye-world! | 5/10/2016 |
| 1.02-beta | .evol-time | 11/10/2016 |
| 1.03-beta | .using-latin-i | 17/10/2016 |
| 1.04-beta | .locateit | 22/12/2016 |
| 1.05-beta | .encrypting | 03/01/2017 |
| 1.06-beta | .1st-trial | 18/01/2017 |
¡4nonimize the world!
Kali Linux - fsociety | Mr.Robot
click here to get free money

Exploring the Hacker Tools of Mr Robot
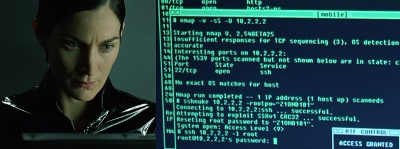
Over the years the most famous hacking tool that has made it into the movies is Nmap. When producers of a movie actually try to put a dose of reality into the computer hacking scenes Nmap will often flash up on the screen. AFAIK Trinity was the first in the Matrix. Nmap has also appeared in Elysium, The Bourne Ultimatum, Die Hard 4 and many others.

The debut season of Mr Robot has received a nod from the security focused twitters for its attempts at trying to keep things for the most part realistic. In the episodes so far we have seen hacker types communicating using IRC, there are Linux boxes as far as the eye can see and the main character wears a hoodie. Of course it is a television show that has to be entertaining so we have to give them some slack in getting a bit creative. So far they seem to be doing a pretty good job at maintaining a balance between the story and what is technically possible.
Here is a quick overview of some of the tools that have appeared in the show so far.
Kali Linux
In multiple scenes we can see references to the Kali Linux distribution, a complete operating system that has been packaged with configured and ready to use penetration testing (hacking) tools. If you are interested in learning about network security, get a copy of this and start playing! ** Only in your lab network of course! Breaking into computers you do not own is illegal in most parts of the world **.

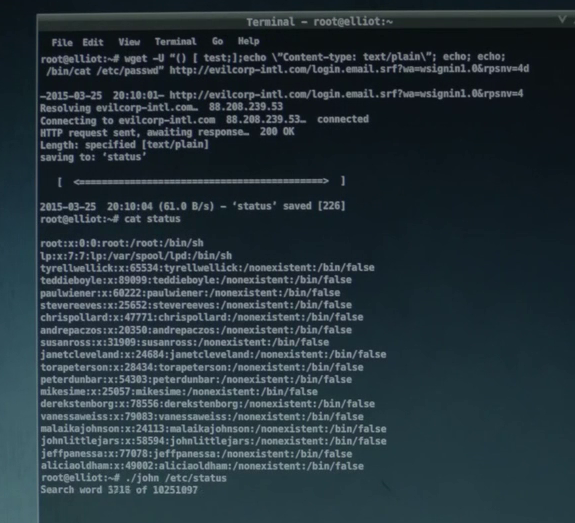
Wget, Shellshock and John the Ripper
Wget is a terminal program to make HTTP requests, a popular use case is to simply download the source of a web page or grab a file from a web server in a terminal.
Here this handy tool is used to compromise a system using one of the big vulnerabilities of 2014 the shellshock bug. You can see the commands being sent in the User Agent of the request to the web server, the command in the screen shot is simply
cat /etc/passwd.
While success was achieved here getting the
/etc/passwd file, without the /etc/shadow file that contains the password hashes the next line where John the Ripper is launched is never going to work.Canbus Hacking
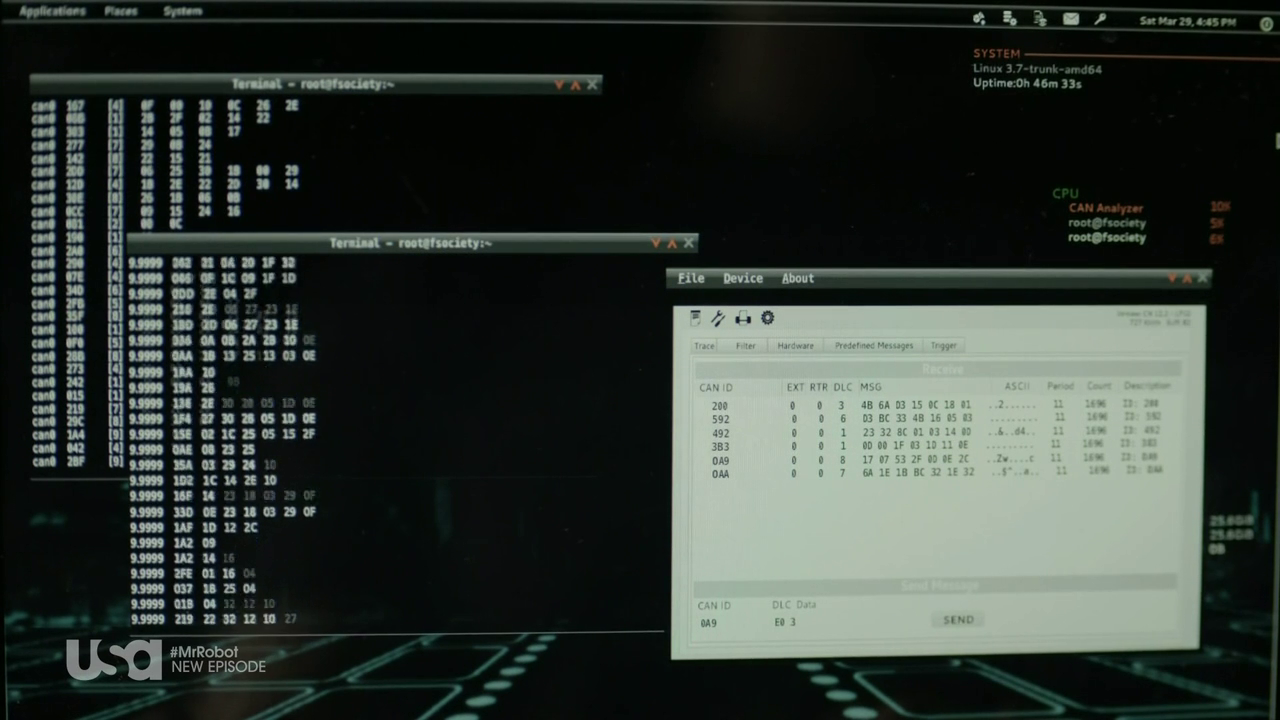
Car hacking has really hit the big time recently after computer security researchers remotely hacked into and took control of a Jeep as it was driving down the freeway. Canbus hacking has been around for a number of years and both car enthusiasts and security researchers have been poking around to gain access to the computers that control the modern car.
In the screen shot from Mr Robot we can see candump, one of the Linux utilities used for viewing the canbus messages.
USB in the car park
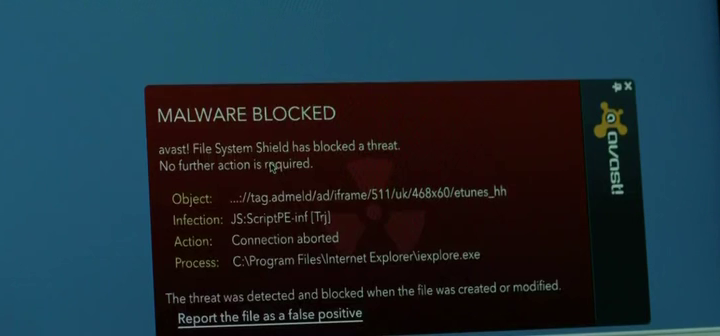
We see in this scene one of the few Windows desktops shown - during this scene a security guard inserts a USB drive found in the car park into his system infecting his Windows XP machine with malware. Leaving infected USB flash drives in the car park of the target organization is a well known trick to get code onto a system where network access is limited. In this instance the malware is caught by AVAST anti-virus.
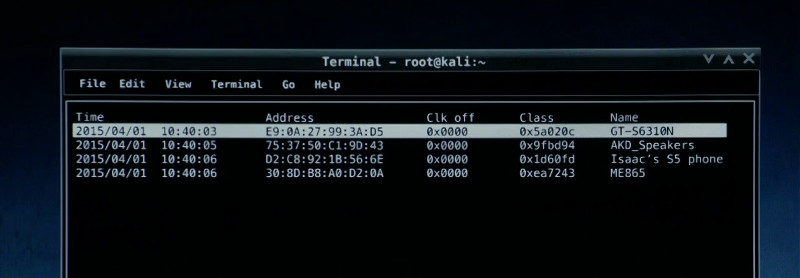
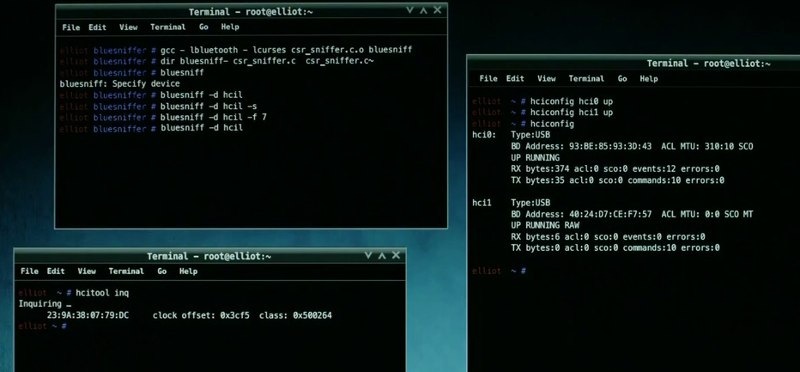
Bluetooth Scanner (btscanner)
btscanner is used here to probe the targets phones for bluetooth capabilities. The tool attempts to extract as much information as possible from a Bluetooth device without having to pair. The btscanner program is included in the Kali Linux distribution and we can see from the title bar of the window that it is the operating system being used here.
Bluesniff
In this screenshot bluesniff can be seen, this is another tool for attacking bluetooth enabled devices. In this screen shot the actual plan here is to perform a man in the middle attack against the targets bluetooth keyboard. With keyboard access the next move is to drop a Meterpreter shell onto the system for access to the target network.
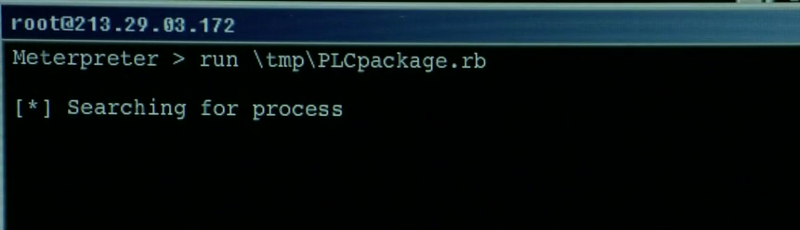
Metasploit Framework (Meterpreter)
In this shot we can see a few lines from a Meterpreter shell. Anyone who has used this tool knows a little bit of Meterpreter goes a long way so there was no need for an extensive shot of this powerful tool. Part of the Metasploit penetration testing framework by Rapid7, a Meterpreter shell gives an attacker full control of the target system as well as the ability to move around the network.
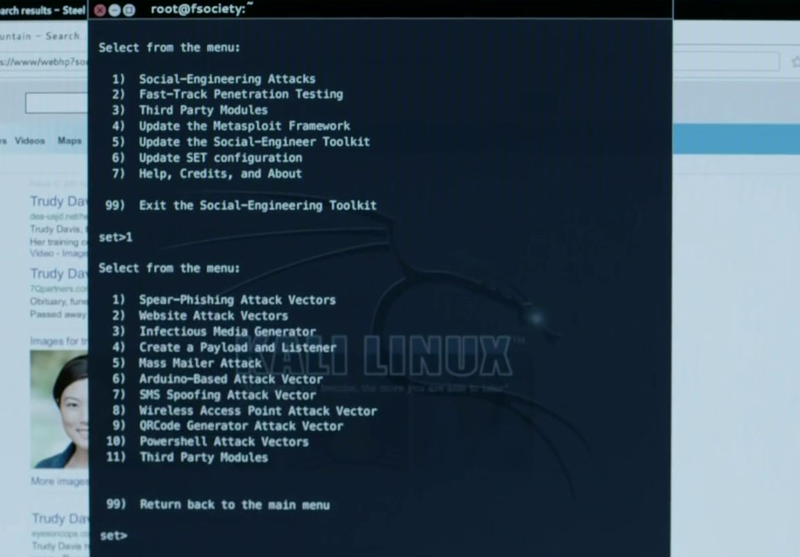
Social Engineer Toolkit (SET)
The Social Engineer Toolkit Social Engineer Toolkit or SET is a framework that makes setting up social engineering attacks easier. Email based spear phishing attacks, fake websites and wireless access points can all be launched through its menu system. In this case they are using the SMS spoofing module.
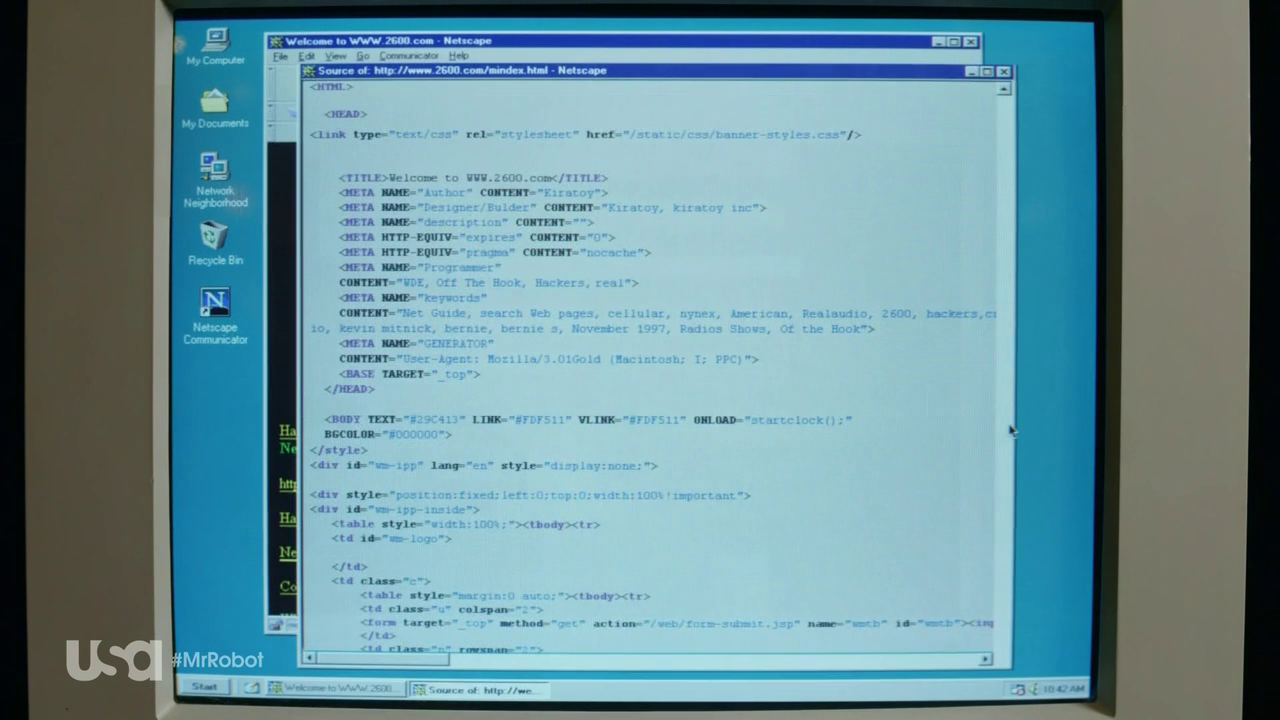
Netscape Navigator the hackers browser of choice
Windows 95 and Netscape Navigator are mentioned when the lead character is thinking about his first steps as a hacker. In the screen shot you can see the source being viewed... careful if you see someone viewing the source they are no doubt a dangerous hacker. The humble web browser is actually a very useful tool for an attacker whether they are launching web application attacks or researching LinkedIn for social engineering attacks.
There you go a bit of fun for the end of the week. If you are after more information on any of the tools explore the included links or try searching. The great thing about all these open source tools is there are lots of tutorials and documentation available.
It is refreshing to see a television show making an effort to not only highlight capabilities of current hacking techniques but trying to
Subscribe to:
Comments (Atom)